The Future of Cybersecurity Resilience: Decoding SaaS Security Playbooks and Market Differentiation in Cloud Identity Management
The cybersecurity landscape in 2025 is defined by a seismic shift toward cloud-first strategies, with identity management emerging as both the linchpin and the weakest link in enterprise security. As organizations accelerate digital transformation, the SaaS security market—valued at $11.2 billion in 2024—is projected to nearly double to $12.23 billion in 2025, driven by a 9.2% compound annual growth rate (CAGR) [1]. This growth is fueled by escalating threats: 58% of organizations struggle to enforce proper privilege levels across SaaS applications, while 46% report difficulty monitoring non-human identities [2]. The stakes are high, and the market is responding with innovative playbooks and differentiation strategies that investors must understand to capitalize on this evolving ecosystem.
The Evolving Threat Landscape: Identity as the New Frontline
Identity has become the primary attack vector in cloud environments. According to the Cloud Security Alliance (CSA), 63% of SaaS breaches in 2025 originate at the identity provider (IdP), with 84% of incidents bypassing multi-factor authentication (MFA) [3]. The proliferation of SaaS-to-SaaS integrations and GenAI tools has expanded the attack surface, with 56% of organizations citing over-privileged API access as a critical risk [4]. Meanwhile, 46% of breaches are linked to weak or exploited MFA protections [5]. These statistics underscore a pressing need for identity-centric security frameworks that prioritize zero-trust principles, dynamic access controls, and real-time monitoring.
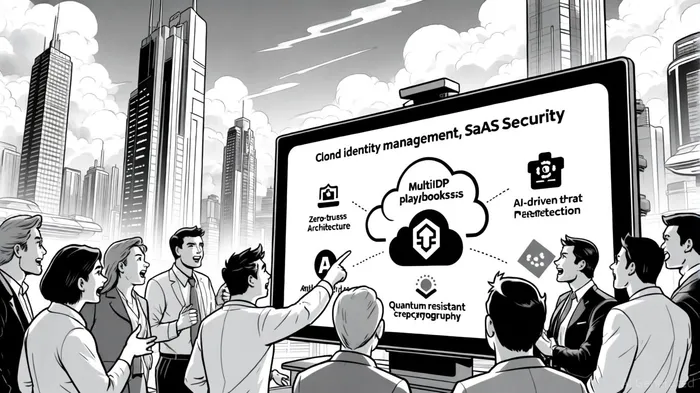
Emerging SaaS Security Playbooks: Zero-Trust and Beyond
Leading vendors are redefining security through structured playbooks. CyberArk's 2025 Identity Security and Cloud Compliance Playbook emphasizes zero standing privileges (ZSP), a model that assumes no user or system has inherent trust. This approach mandates continuous verification of access requests, reducing the risk of credential misuse and lateral movement [6]. Similarly, the CSA advocates for the Insight to Action framework, which integrates risk reduction strategies with compliance requirements, enabling organizations to automate policy enforcement across hybrid and multi-cloud environments [7].
A critical component of these playbooks is identity hardening, which includes enforcing MFA, isolating admin accounts, and eliminating legacy trust paths. For instance, 97% of organizations now prefer centralized dashboards for unified cloud security platforms, streamlining policy configuration and enhancing visibility [8]. These frameworks are not merely reactive; they are proactive, leveraging AI to predict and mitigate risks before breaches occur.
Market Differentiation: The Rise of AI-Driven and Multi-IDP Strategies
To stand out in a crowded market, SaaS security vendors are adopting advanced differentiation strategies. Multi-identity provider (multi-IDP) architectures are gaining traction, allowing organizations to avoid vendor lock-in and tailor identity solutions to specific use cases. OktaOKTA-- and Ping Identity lead this trend, offering robust identity orchestration tools to unify access control across disparate systems [9]. These architectures are particularly valuable in mergers and acquisitions, where integration complexity demands interoperable solutions.
Another frontier is event-driven identity systems, which enable real-time adaptations to contextual threats. The standardization of the Continuous Access Evaluation Protocol (CAEP) allows dynamic responses such as session revocation or additional authentication triggers based on risk signals [10]. For example, Barracuda Networks uses AI to monitor email activity for account takeover attempts, while Abnormal Security's AI Security Mailbox automates threat response [11].
AI-powered identity threat detection and response (ITDR) is also reshaping the landscape. 96% of security professionals expect AI to play a pivotal role in combating identity-based breaches [12]. Vendors like CrowdStrike and Inky leverage generative AI to analyze user behavior and detect anomalies, reducing the burden on security teams.
Passwordless Authentication and Quantum-Resilient Cryptography
The decline of password-based systems is accelerating, with the passwordless authentication market projected to grow from $923.3 million in 2024 to $8.9 billion by 2033 [13]. FIDO2 and WebAuthn standards are becoming the norm, using public/private key cryptography to eliminate shared secrets. Major platforms like Apple and Google now support passkey-based authentication, offering a user-friendly alternative to traditional passwords.
Looking ahead, post-quantum cryptography (PQC) is emerging as a critical differentiator. The National Institute of Standards and Technology (NIST) standardized PQC algorithms in August 2024, prompting vendors to adopt cryptographic agility strategies [14]. This shift is essential for future-proofing identity systems against quantum computing threats.
Investment Implications: Where to Allocate Capital
The IAM market is expected to reach $24 billion by 2025, growing at a 13% annual rate [15]. Investors should prioritize platforms that combine zero-trust architecture, AI-driven threat detection, and multi-IDP interoperability. Key players like SailPointSAIL-- and Saviynt are expanding their offerings to address both human and machine identities, with SailPoint excelling in hybrid environments and Saviynt dominating cloud-native deployments [16].
Moreover, the rise of SaaS Security Posture Management (SSPM) and Cloud-Native Application Protection Platforms (CNAPPs) highlights the demand for unified solutions. 67% of organizations now implement CSPM, while 62% adopt CNAPPs to automate compliance and threat mitigation [17]. These platforms are critical for managing the complexity of multi-cloud environments and ensuring regulatory alignment.
Conclusion: The Path to Resilience
As the cloud security landscape evolves, organizations must adopt identity-centric playbooks that integrate zero-trust, AI, and passwordless authentication. Vendors that lead in multi-IDP architectures, event-driven systems, and quantum resilience will dominate the market. For investors, the opportunity lies in platforms that not only address today's threats but also anticipate tomorrow's challenges—transforming identity from a vulnerability into a strategic asset.

Comentarios
Aún no hay comentarios